How We Protect Your AI Interactions
Every AI request flows through our robust policy enforcement engine, ensuring real-time compliance, auditing, and control
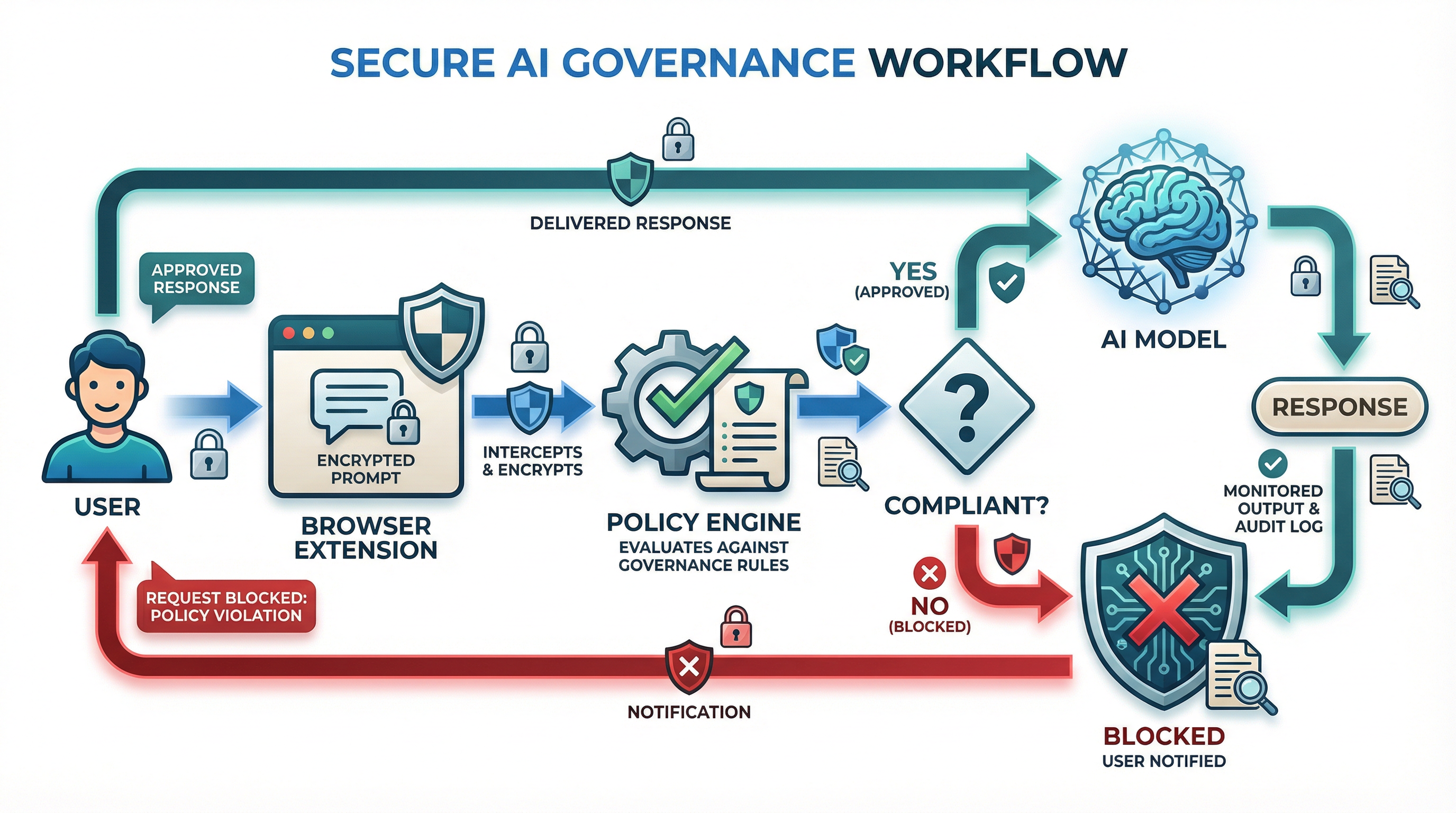
Every AI request flows through our robust policy enforcement engine, ensuring real-time compliance, auditing, and control

We collect only the data required to operate the service and enforce your governance policies. Your data is never used for any other purpose.
Customer data is never used to train AI models - yours or anyone else's. Your prompts, responses, and policies remain completely private.
Set your own data retention policies. Export audit logs at any time. Delete data on demand. You control how long we keep your information.
Transparent data practices with complete audit trails. Know exactly what data we have and how it's used. Export logs in multiple formats.
GDPR, CCPA, PIPEDA, and other privacy regulations built into our platform architecture. Data residency options available.
Enterprise customers can deploy containment.ai on-premise or in air-gapped environments. Complete data sovereignty with offline policy enforcement for the highest security requirements.
Our privacy team is here to answer any questions about data handling, retention, or compliance.
privacy@containment.ai →Security isn't a feature - it's the foundation of everything we build. Our platform is designed with defense-in-depth principles from the ground up.
AES-256 encryption at rest, TLS 1.3 in transit. All data is encrypted before it touches disk. Key rotation and HSM protection included.
SSO/SAML, multi-factor authentication (MFA), and granular role-based access controls (RBAC). Support for hardware security keys.
Secure SDLC with automated SAST/DAST scanning, dependency monitoring, and code review requirements. Security training for all engineers.
Annual independent audits, quarterly penetration testing, and continuous vulnerability scanning. Third-party security assessments.
Security operations center (SOC) with real-time threat detection and automated incident response. 99.99% uptime SLA.
Continuous vulnerability scanning, automated patching, and a responsible disclosure program. Bug bounty program coming soon.
Report security vulnerabilities directly to our security team. We take all reports seriously.
security@containment.ai →We are actively pursuing these certifications and building our platform to meet these rigorous standards from day one
Access our security documentation, compliance reports, and legal agreements
Containment by Design - ten principles for securing AI systems that reason, adapt, and act autonomously.
Independent audit report covering security, availability, and confidentiality controls.
Comprehensive compliance guides for HIPAA, GDPR, FedRAMP, and other regulatory frameworks.
Our security and compliance teams are here to help. Reach out with any questions about our practices, certifications, or how we can meet your specific requirements.
Contact Security Team Contact Compliance Team